Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Logical Operations CyberSec First Responder CFR-210 Questions and answers with ExamsMirror
Exam CFR-210 Premium Access
View all detail and faqs for the CFR-210 exam
725 Students Passed
86% Average Score
91% Same Questions
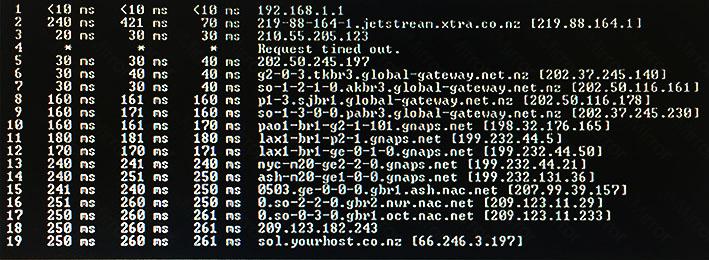
Click the exhibit button. Which of the following Windows tools is executed?
Which of the following is an automated password cracking technique that uses a combination of upper and lower case letters, 0-9 numbers, and special characters?
An analyst would like to search for a specific text string at the beginning of a line that begins with four capital alphabetic characters. Which of the following search operators should be used?
Which of the following resources BEST supports malware analysis?
An organization’s firewall has recently been bombarded with an excessive amount of failed requests. A security analyst has been tasked with providing metrics on any failed attempts to ports above 1000. Which of the following regular expressions will work BEST to identify an IP address with the desired port range?
Log review shows that large amounts of data are being sent to an IP address unassociated with the company. Which of the following migration techniques should be implemented?
An outside organization has reported to the Chief Information Officer (CIO) of a company that it has received attack from a Linux system in the company’s DMZ. Which of the following commands should an incident responder use to review a list of currently running programs on the potentially compromised system?
During the identification phase, it is discovered that port 23 is being used maliciously. Which of the following system hardening techniques should be used to remediate the issue?
Which of the following enables security personnel to have the BEST security incident recovery practices?
A suspicious laptop is found in a datacenter. The laptop is on and processing data, although there is no application open on the screen. Which of the following BEST describes a Windows tool and technique that an investigator should use to analyze the laptop’s RAM for working applications?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
