Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the Cisco CCNA 200-301 Questions and answers with ExamsMirror
Exam 200-301 Premium Access
View all detail and faqs for the 200-301 exam
760 Students Passed
86% Average Score
97% Same Questions
What is the function of a controller in controller-based networking?
What is a DHCP client?
Which WAN topology provides a combination of simplicity quality, and availability?
A manager asks a network engineer to advise which cloud service models are used so employees do not have to waste their time installing, managing, and updating software which is only used occasionally Which cloud service model does the engineer recommend?
Refer to the exhibit.
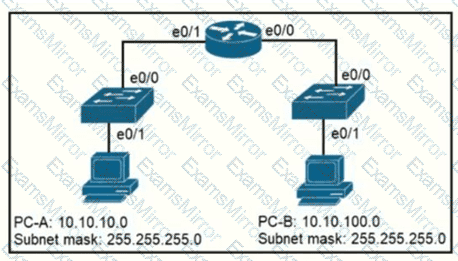
When PC-A sends traffic to PC-B, which network component is in charge of receiving the packet from PC-A verifying the IP addresses, and forwarding the packet to PC-B?
What are two benefits of controller-based networking compared to traditional networking?
In QoS, which prioritization method is appropriate for interactive voice and video?
Which protocol does an IPv4 host use to obtain a dynamically assigned IP address?
Which command enables a router to become a DHCP client?
Which command entered on a switch configured with Rapid PVST* listens and learns for a specific time period?
Which two functions are performed by the core layer in a three-tier architecture? (Choose two)
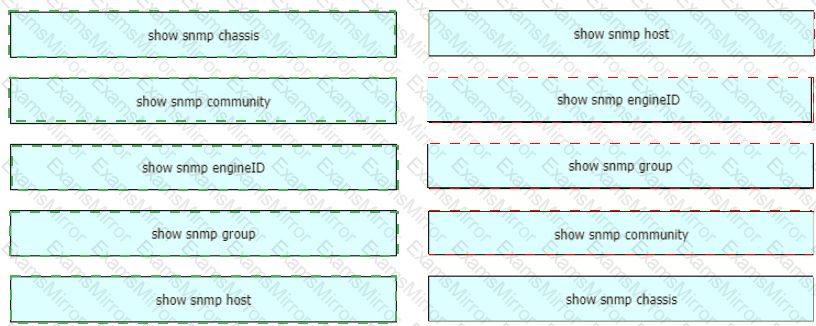
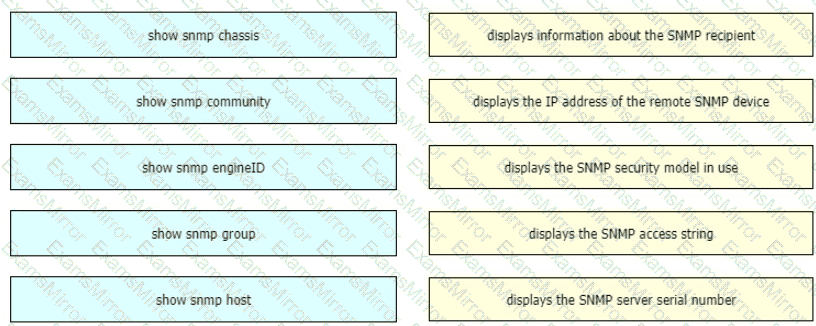
Drag and drop the SNMP manager and agent identifier commands from the left onto the functions on the right
What are two functions of a Layer 2 switch? (Choose two)
Which 802.11 management frame type is sent when a client roams between access points on the same SSID?
Refer to the exhibit.
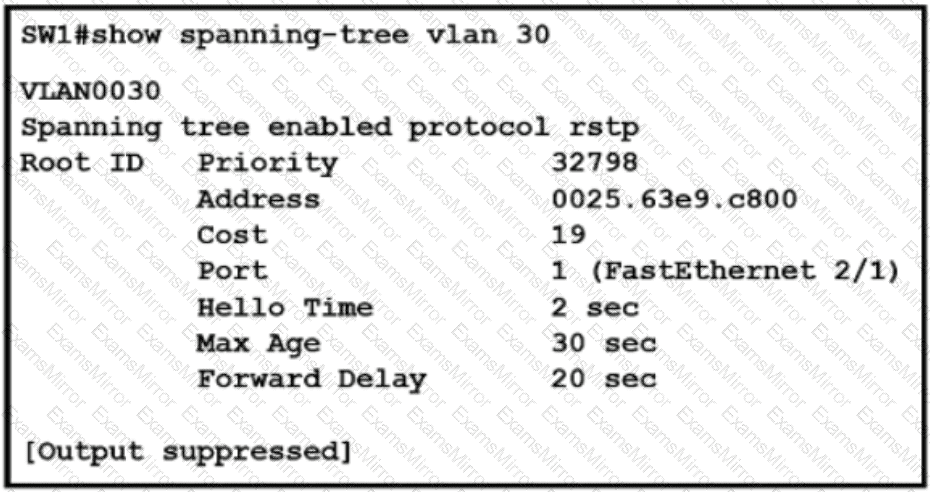
What two conclusions should be made about this configuration? (Choose two )
When a site-to-site VPN is configured, which IPsec mode provides encapsulation and encryption of the entire original P packet?
Which API is used in controller-based architectures to interact with edge devices?
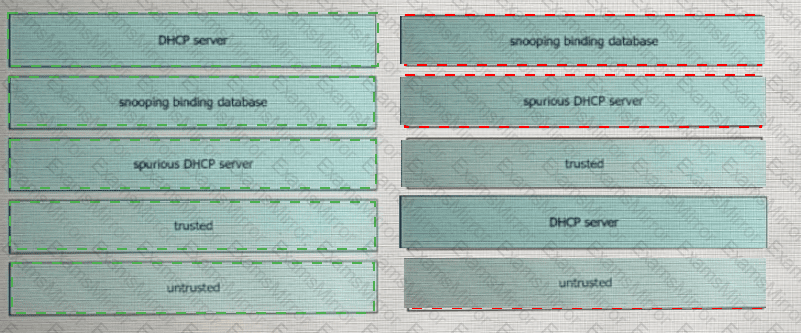
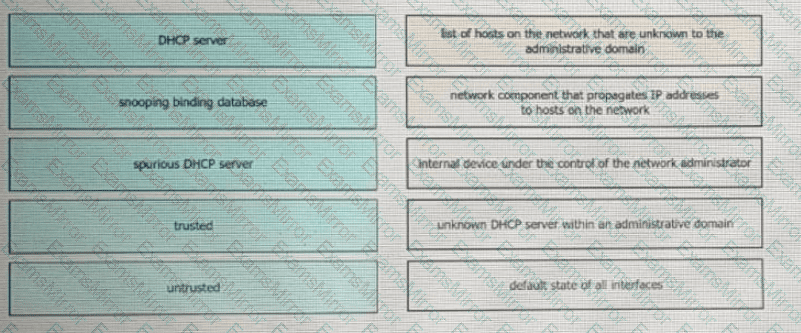
Drag and drop the DHCP snooping terms from the left onto the descriptions on the right.
Which function does the range of private IPv4 addresses perform?
What does a router do when configured with the default DNS lookup settings, and a URL is entered on the CLI?
Which technology is used to improve web traffic performance by proxy caching?
What is recommended for the wireless infrastructure design of an organization?
When implementing a router as a DHCP server, which two features must be configured'? (Choose two)
Which configuration ensures that the switch is always the root for VLAN 750?
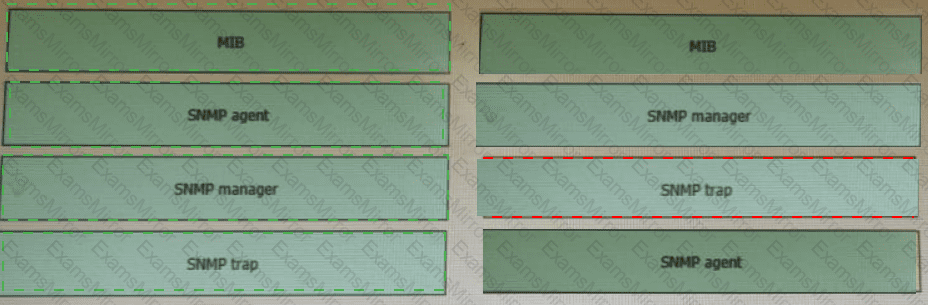
Drag and drop the SNMP components from the left onto the descriptions on the right.

What protocol allows an engineer to back up 20 network router configurations globally while using the copy function?
Refer to the exhibit.
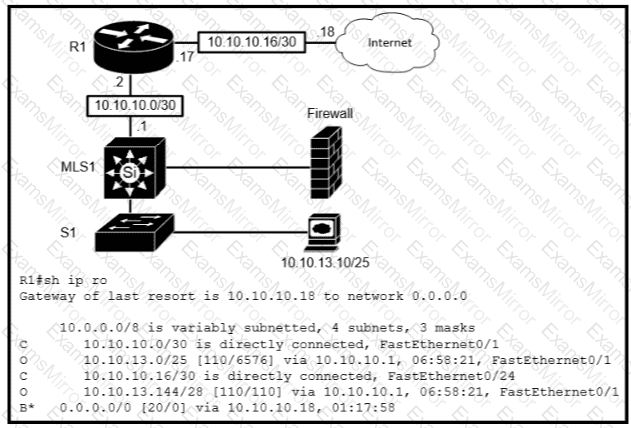
Which type of route does R1 use to reach host 10.10.13.10/32?
When configuring IPv6 on an interface, which two IPv6 multicast groups are joined? (Choose two)
What is a characteristic of a SOHO network?
Which device performs stateful inspection of traffic?
How does HSRP provide first hop redundancy?
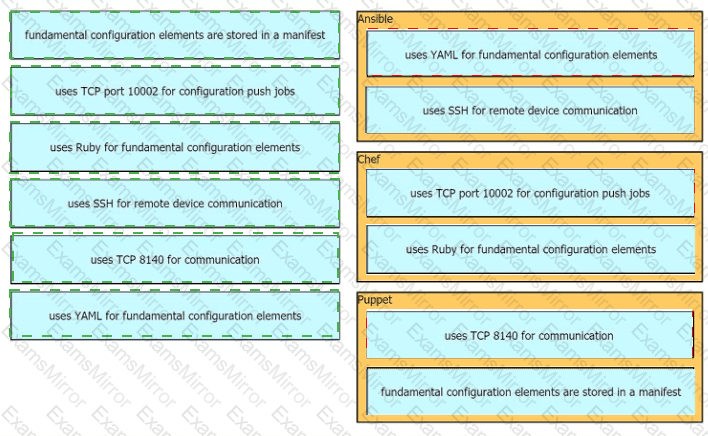
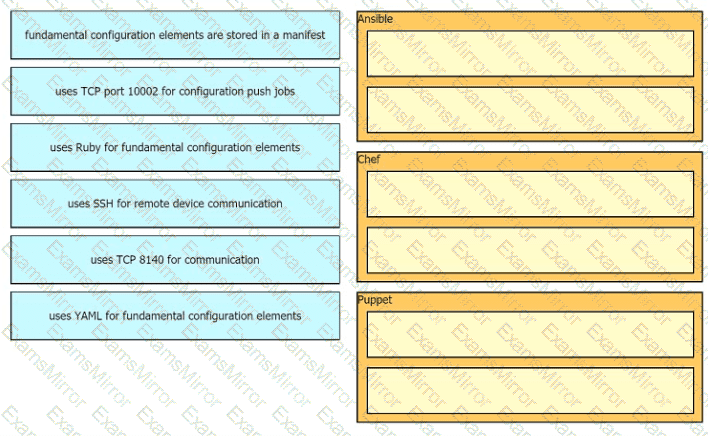
Drag drop the descriptions from the left onto the correct configuration-management technologies on the right.
Which statement identifies the functionality of virtual machines?
What is a benefit of using a Cisco Wireless LAN Controller?
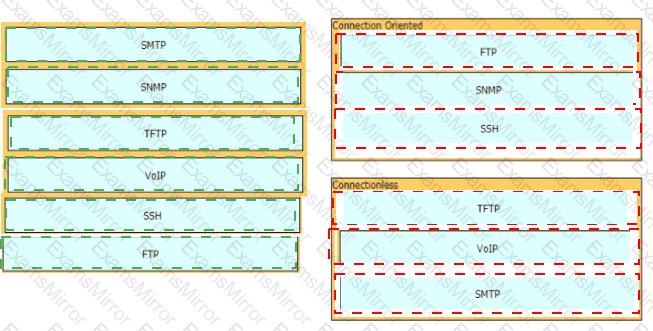
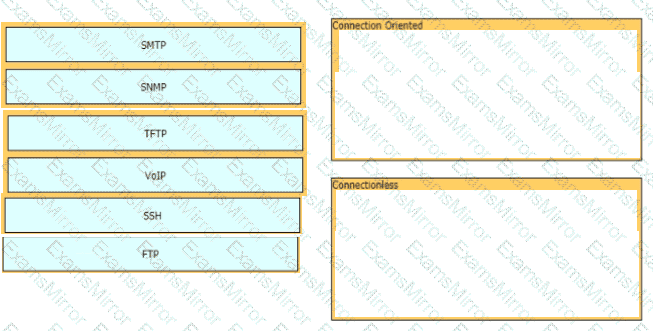
Drag and drop the network protocols from the left onto the correct transport services on the right.
What is a recommended approach to avoid co-channel congestion while installing access points that use the 2.4 GHz frequency?
What occurs when overlapping Wi-Fi channels are implemented?
Refer to the exhibit.
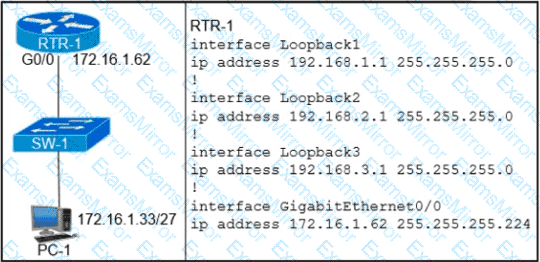
Which configuration on RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
Which two encoding methods are supported by REST APIs? (Choose two)
How will Link Aggregation be Implemented on a Cisco Wireless LAN Controller?
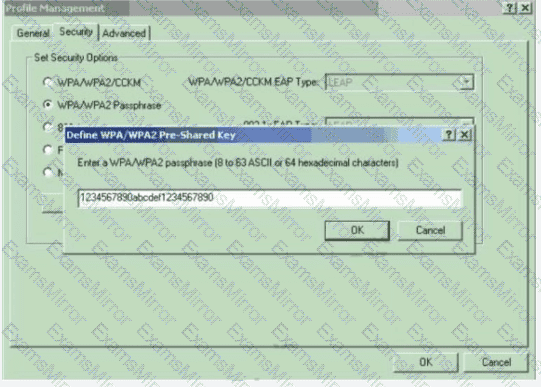
Which type of wireless encryption is used for WPA2 in preshared key mode?
Refer to the exhibit.
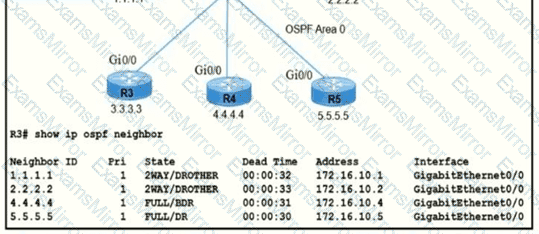
R5 is the current DR on the network, and R4 is the BDR. Their interfaces are flapping, so a network engineer wants the OSPF network to elect a different DR and BDR. Which set of configurations must the engineer implement?
A)

B)

C)

D)

Which QoS Profile is selected in the GUI when configuring a voice over WLAN deployment?
A network administrator must enable DHCP services between two sites. What must be configured for the router to pass DHCPDISCOVER messages on to the server?
What are two southbound APIs? (Choose two )
How do servers connect to the network in a virtual environment?
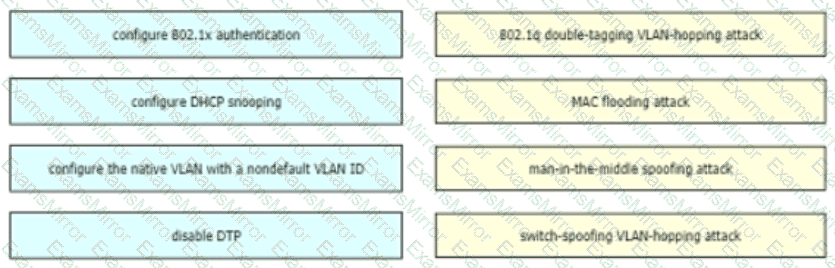
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
How do TCP and UDP differ in the way they provide reliability for delivery of packets?
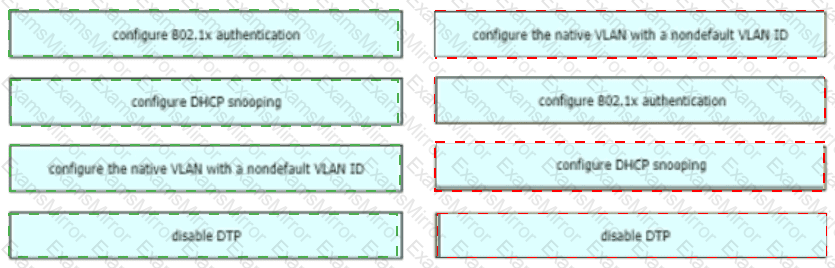
How are VLAN hopping attacks mitigated?
Which HTTP status code is returned after a successful REST API request?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.