Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Security Administration GPEN Questions and answers with ExamsMirror
Exam GPEN Premium Access
View all detail and faqs for the GPEN exam
662 Students Passed
94% Average Score
97% Same Questions
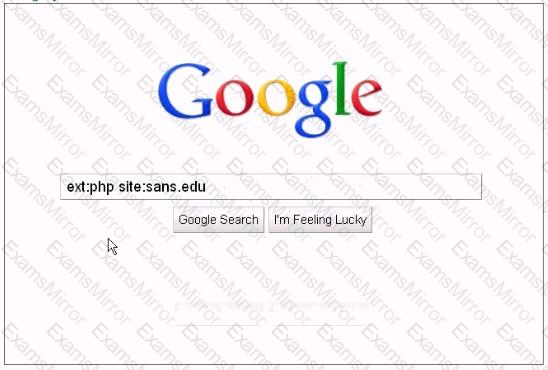
Analyze the screenshot below, which of the following sets of results will be retrieved using this search?
Which of the following is the frequency range to tune IEEE 802.11a network?
You have obtained the hash below from the /etc/shadow file. What are you able to discern simply by looking at this hash?
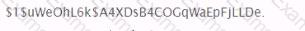
Peter, a malicious hacker, obtains e-mail addresses by harvesting them from postings, blogs, DNS listings, and Web pages. He then sends large number of unsolicited commercial e-mail (UCE) messages on these addresses. Which of the following e-mail crimes is Peter committing?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He enters the following command on the
Linux terminal:chmod 741 secure.c
Considering the above scenario, which of the following statements are true?
Each correct answer represents a complete solution. Choose all that apply.
You have forgotten your password of an online shop. The web application of that online shop asks you to enter your email so that they can send you a new password. You enter your email you@gmail.com' and press the submit button. The Web application displays the server error.
What can be the reason of the error?
Which of the following statements are true about NTLMv1?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Penetration tester in the Secure Inc. Your company takes the projects to test the security of various companies. Recently, Secure Inc. has assigned you a project to test the security of a Web site. You go to the Web site login page and you run the following SQL query:
SELECT email, passwd, login_id, full_name
FROM members
WHERE email = 'attacker@somehwere.com'; DROP TABLE members; --'
What task will the above SQL query perform?
You want to search the Apache Web server having version 2.0 using google hacking. Which of the following search queries will you use?
You run the rdisk /s command to retrieve the backup SAM file on a computer. Where should you go on the computer to find the file?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
