Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Security Administration GSEC Questions and answers with ExamsMirror
Exam GSEC Premium Access
View all detail and faqs for the GSEC exam
670 Students Passed
84% Average Score
97% Same Questions
Which of the following protocols implements VPN using IPSec?
What cryptographic technique does file Integrity monitoring employ?
What type of attack can be performed against a wireless network using the tool Kismet?
Which of the following are advantages of Network Intrusion Detection Systems (NIDS)?
Which of the following quantifies the effects of a potential disaster over a period of time?
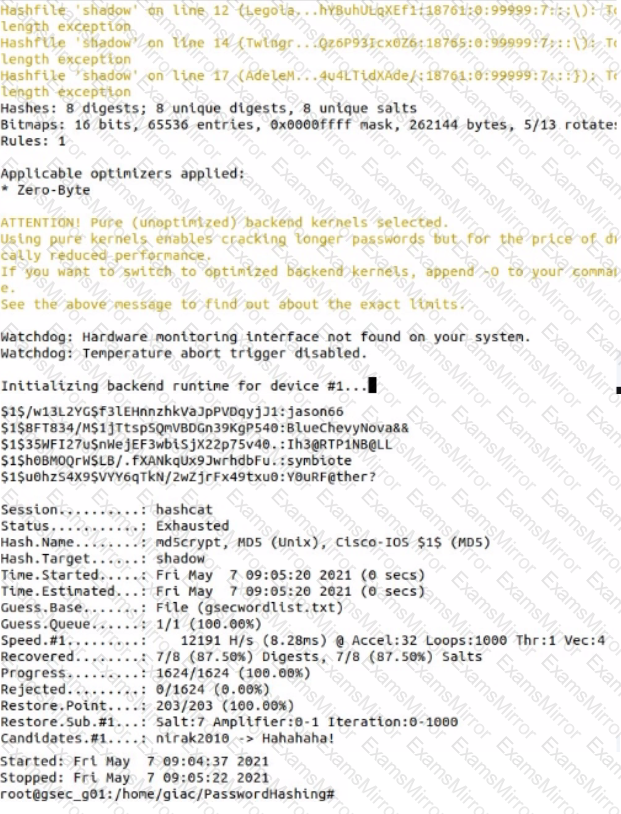
Use Hashcat to crack a local shadow file. What Is the password for the user account AGainsboro?
Hints
• The shadow file (shadow) and Hashcat wordlist (gsecwordlist.txt) are located in the directory /home /giac /PasswordHashing/
• Run Hashcat in straight mode (flag -a 0) to crack the MD5 hashes (flag -m 500) In the shadow file.
• Use the hash values from the Hashcat output file and the shadow file to match the cracked password with the user name.
• If required, a backup copy of the original files can be found in the shadowbackup directory.

When trace route fails to get a timely response for a packet after three tries, which action will it take?
Which of the following tasks is the responsibility of a Linux systems administrator who is deploying hardening scripts to his systems?
What is a limitation of deploying HIPS on a workstation?
Which of the following areas of a network contains DNS servers and Web servers for Internet users?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
