Spring Special Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = getmirror
Pass the GIAC Security Administration GCIA Questions and answers with ExamsMirror
Exam GCIA Premium Access
View all detail and faqs for the GCIA exam
652 Students Passed
90% Average Score
92% Same Questions
Which of the following protocols does IPsec use to perform various security functions in the network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is used to provide a protective shield for the data passing over the Internet?
Which of the following switches is used with Pslist command on the command line to show the statistics for all active threads on the system, grouping these threads with their owning process?
Which of the following is an expression of interference that triggers a false positive signal during an intrusion detection process performed by IDS?
Which of the following types of write blocker device uses one interface for one side and a different one for the other?
Which of the following is not a valid Failed Logon EventID?
Which of the following is an open-source Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software?
You work as a Network Administrator for McRobert Inc. Your company has a Windows NT 4.0 TCP/IP-based network. You want to list the cache of NetBIOS names and IP addresses. Which of the following utilities will you use?
Which of the following networks relies on the tunneling protocol?
Victor is a novice Ethical Hacker. He is learning the hacking process, i.e., the steps taken by malicious hackers to perform hacking. Which of the following steps is NOT included in the hacking process?
Which of the following is true for XSS, SQL injection, and RFI?
Which of the following is used to provide a protective shield for the data passing over the Internet?
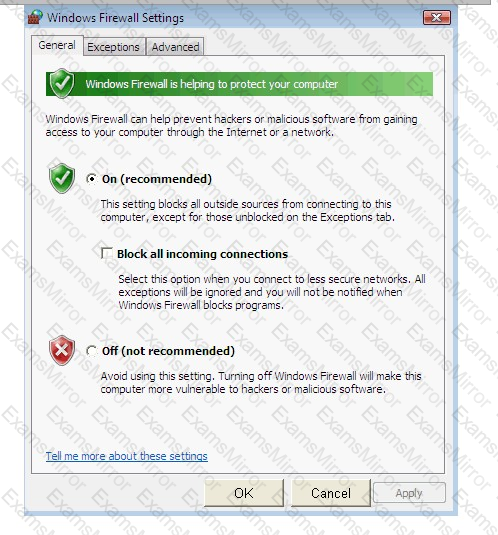
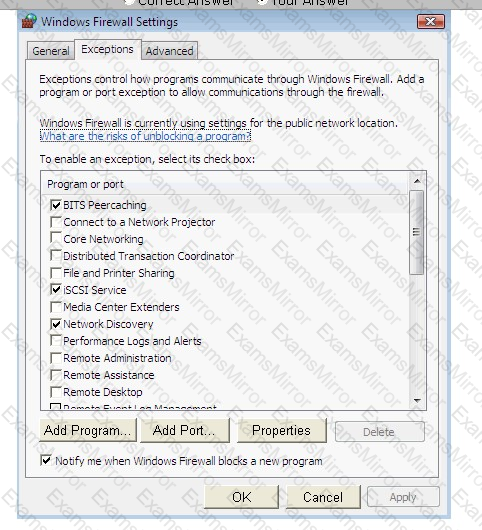
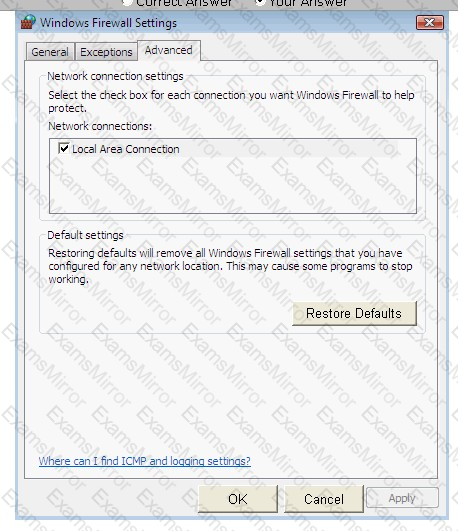
Steve works as a Network Administrator for Blue Tech Inc. All client computers in the company run the Windows Vista operating system. He often travels long distances on official duty. While traveling, he connects to the office server through his laptop by using remote desktop connection.
He wants to run an application that is available on the server of the company. When he connects to the server, he gets a message that the connection is blocked by the firewall. He returns to his office to resolve the issue. He opens the Windows Firewall Settings dialog box. What actions should he perform in the dialog box given below to accomplish the task?
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following wireless security features provides the best wireless security mechanism?
TOP CODES
Top selling exam codes in the certification world, popular, in demand and updated to help you pass on the first try.
